Answering Key Questions About Security Risk Assessments
Discover what is the security risk assessment, who needs it, why, and how often. Explore key questions on security risk assessment for robust cyber defense Security risk assessment is critical for safeguarding organizational assets, and therefore, it is actively applied within security management or as part of security frameworks and regulations. Risk assessment is a systematic process that involves identifying, analyzing, and evaluating potential threats and vulnerabilities to an organization's information assets. The primary goal of the risk assessment in the context of information security is understanding the potential impact of threats, the likelihood of their occurrence, and the effectiveness of existing safeguards. In this article, we delve deeper into the idea of risk assessment by answering the following key questions:
- What is a security risk assessment?
- What is the difference between vulnerability, threat, and risk?
- Who needs a risk assessment?
- How often should risk assessments be conducted?
- Why need the risk assessment?
- What are the risk assessment methodologies? Comparing NIST 800-30 vs. ISO 27005 vs. OCTAVE Allegro.
Continue reading to learn more.
What is a Security Risk Assessment?
The NIST 800-30 Special Publication defines risk assessment as a “systematic process that addresses the undesirable adverse impacts to organizational assets, operations, and individuals […] arising from the operation and use of information systems (p.15)”. Risk assessment helps determine risks that are common to the organization’s electronic and physical assets and provides a stable background for mitigating the identified risks.
What is the Difference Between Vulnerability, Threat, and Risk?
Risk assessment is a complex phenomenon that unites several important concepts under its umbrella. The main ones are “vulnerability,” “threat,” “risk,” “likelihood,” and “impact.” The standard definitions for these terms may also be found in the NIST SP 800-30, and each of them can be adapted within the context of any organization that deals with sensitive information. Thus, as defined in NIST 800-30:
- Vulnerability “is a flaw or weakness in system security procedures, design, implementation, or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or a violation of the system’s security policy (p. 15).”
Organizations may have non-technical vulnerabilities related to ineffective guidelines, procedures, policies, or standards and technical ones related to information systems weaknesses. Both types of vulnerability could potentially result in a security incident.
- Threat “is the potential for a person or thing to exercise (accidentally trigger or intentionally exploit) a specific vulnerability (p.12).”
Organizational information systems and people may be under several types of threat, which are generally grouped into natural, human, and environmental.
- Likelihood refers to the probability that a given threat event is capable of exploiting a given vulnerability (or set of vulnerabilities) (p. 21).”
Depending on the capability of the threat agent and the effectiveness of preventive controls, the likelihood can be described as high, medium, or low.
- Impact is the result of a “successful threat exercise of a vulnerability (p. 21)”
Impact is determined by the consequences to the organization of a successful threat event. Just like likelihood, it may be measured as high, medium, or low. When the above concepts are defined, the understanding of the security risk assessment becomes clearer.
- Risk is “the net mission impact considering (1) the probability that a particular threat will trigger or exploit a particular vulnerability and (2) the resulting impact on the organization if this should occur.
Risks to organizations and their information systems arise due to unauthorized modification, disclosure, or destruction of information; unintentional errors; IT disruptions; and/or organizational failure to exercise diligence in implementing and operating IT systems and business processes. In the context of a particular organization, risk assessment pertains to identifying risks that are specific to its operating environment. The best way to approach the organization’s need for information security is a properly contextualized risk assessment that involves identifying threats, classifying organizational assets, and rating system vulnerabilities. These measures provide key information and guidelines to implement effective controls and avoid security incidents.
Who Needs a Risk Assessment?
Security risk assessments are essential for various entities across different sectors for many reasons. First, organizations fall under the scope of certain data security rules, regulations, and security standards. For example, organizations covered by HIPAA and PCI DSS are required to assess their risks regularly. Otherwise, they are at risk of non-compliance fines and reputational damages. Risk assessments are also required for all security-focused audits and certifications, such as ISO 27001, SOC 2, and HITRUST. Second, private businesses that want to understand their main risks and prioritize security controls. Private businesses that do not process regulated data and do not fall under the scope of rules and regulations above will also benefit from the information security risk assessment. Like any other organization, private businesses face diverse cyber threats, including data breaches, ransomware attacks, intellectual property theft, etc. Regular security risk assessments benefit organizations by not only identifying potential threats but also helping to uncover vulnerabilities within their systems, applications, and processes. By understanding their threats and vulnerabilities, businesses can understand their main risks and prioritize controls to mitigate these risks. Finally, government agencies and their contractors whose activity is crucial for national security. These organizations manage vast amounts of sensitive information and provide essential public services. Risk assessments are vital for identifying potential threats to national security, critical infrastructure, and public safety In essence, the dynamic cybersecurity landscape, coupled with regulatory requirements and the increasing interconnectivity of systems, necessitates the adoption of risk assessment practices across various sectors. By identifying, evaluating, and mitigating risks, organizations can enhance their resilience against cyber threats and ensure the continuity of their operations.
How Often Should Risk Assessments Be Conducted?
Risk assessment is not a one-time activity that provides permanent information for organizational decision-makers. Rather, organizations employ an ongoing process as part of their risk management strategy. It is generally recommended that risk assessments be conducted at least annually and in response to significant changes and trigger events in business processes, personnel, and/or technologies.
Why is a Risk Assessment Important?
Advancements in technology and a shifting security landscape expose organizations to greater security risks every day. Risk assessment allows organizations to identify possible information security risks that could result in malicious acts, operational failures, data breaches, and non-compliance. See how security risk assessments contribute to addressing these risks. First, risk assessments help organizations identify vulnerabilities in their data, systems, networks, and processes. This, in turn, helps detect potential threats that may exploit these vulnerabilities. By understanding their vulnerabilities and threats, businesses can take steps to strengthen security measures and reduce the risk of exploitation. In addition, risk assessments help prevent data breaches that are always damaging to organizations' finances, reputation, and compliance. For instance, an appropriate risk assessment would possibly help prevent one of the largest health data breaches in the history of the U.S. It occurred when a series of cyberattacks against Anthem Inc. exposed the electronic health information of 79 million people, resulting in a $16 million settlement. This, and many other examples, demonstrate that risk assessment is an essential factor in information security management. Second, risk assessments are crucial to maintaining compliance, as was already mentioned before. Regular risk assessments are essential to comply with laws and standards such as GDPR, HIPAA, PCI DSS, and others. Failure to conduct the risk assessment may result in general non-compliance and undesired security incidents. Both conditions significantly damage the organization's reputation and may be costly for businesses. For instance, according to the 2024 OCR Report on HIPAA compliance, there is a continued need for regulated entities to improve their risk assessment and risk management practices. Third, risk assessment improves organizations' decision-making. Risk assessments provide insights into the organization's vulnerabilities and potential threats. Armed with this information, decision-makers can allocate resources more effectively. They can prioritize investments in security measures that address the most critical risks, ensuring that limited resources are used where they can have the greatest impact. Fourth, risk assessments contribute to business continuity planning. Organizations can develop strategies to maintain essential functions during and after a security incident or business disruption by understanding potential threats. Finally, security risk assessment helps demonstrate a commitment to information security and build trust with customers, partners, and stakeholders. Proactively addressing security concerns fosters confidence in the organization's ability to protect sensitive information.
What are the Security Risk Assessment Methodologies?
multidimensional process involving analyzing multiple technologies, people, processes, and their interactions. That is why businesses need a risk assessment methodology that would guide them through the risk assessment process smoothly. NIST 800-30 and ISO 27005 are the most frequently used risk assessment methodologies. Let’s digest each of them:
NIST SP 800-30
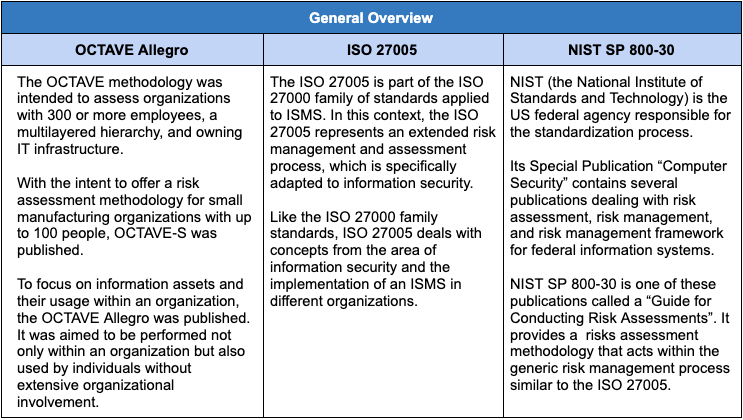
General overview.NIST SP 800-30, titled "Guide for Conducting Risk Assessments," is considered one of the most widely used security risk assessment guidelines. It provides an all-encompassing framework for conducting risk assessments by federal and private organizations. The NIST risk assessment guidelines assist businesses in improving their capacity to thwart, identify, and react to cyber-related threats and reduce the organization’s overall risk exposure. NIST three-tier approach. NIST recommends a three-tier approach to applying risk assessment and management processes throughout the organization:
- Tier 1. Organization’s level: involves risk assessment activities applied to the organization as a whole, including policies, regulations, guidelines, and strategic weaknesses.
- Tier 2. Business processes: addresses risks in relation to the organization’s mission and business processes. It also takes into consideration organizational resilience (the number of information systems, how they are integrated into the overall enterprise architecture, and which potential risks and threats might arise).
- Tier 3. Information systems: the most applied because it focuses on risks from an IS perspective. The main aim of Tier 3 is to identify and describe vulnerabilities within the specific IS, estimate the risks related to them, and categorize and prioritize these systems.
Process. The NIST 800-30 risk assessment process entails 4 main steps.
- Prepare for assessment to establish a context for the risk assessment - purpose, scope, and scoring model.
- Conduct an assessment to identify threat sources and vulnerabilities; determine the likelihood of occurrence, magnitude of impact, and the risk itself.
- Communicate results with a comprehensive risk assessment report documenting all the assessment results and recommendations
- Maintain the assessment on a regular basis
Read NIST risk assessment guidelines to learn more about the risk assessment as per NIST 800-30.
ISO 27005
General overview. The ISO 27005 is part of the ISO 27000 family of standards applied to ISMS. In this context, ISO 27005 represents an extended risk management and assessment process specifically adapted to information security. Like the ISO 27000 family standards, ISO 27005 deals with concepts related to information security and the implementation of an ISMS in different organizations. Concept and Framework. The ISO 27005 risk assessment can be carried out on the level of the entire company, its organizational units (i.e., department, location), every IT system (either existing or planned), or regarding specific issues (i.e., business continuity planning). However, to work properly, the ISO 27005 risk management process requires full support from the organization’s management. Process description:
- Context establishment
- Risk assessment (identification, analysis, evaluation)
- Risk treatment (modification, retention, avoidance, sharing)
- Risk Acceptance
- Risk communication and consultation
- Information security risk monitoring and review
OCTAVE Allegro
General overview. The OCTAVE framework was intended to assess organizations with 300 or more employees, a multilayered hierarchy, and owning IT infrastructure. With the intent to offer a risk assessment methodology for small manufacturing organizations with up to 100 people, OCTAVE‐S was published. The OCTAVE Allegro was published to focus on information assets and their usage within an organization. It was aimed to be performed within an organization and used by individuals without extensive organizational involvement. Concept and framework. The original OCTAVE method is divided into three phases: Phase 1 focuses on identifying the organization’s information‐related assets. A clear vision of these assets is helpful for compiling the potential threats and security measures to counter them. Phase 2 performs a threat analysis on the technical aspects of the assets identified in the previous phase and collects technical vulnerabilities for the organization’s key components. The asset and threat analysis results are applied in Phase 3 when the potential risks arising from the vulnerabilities are analyzed. The third phase also identifies protection strategies for reducing these risks and thus implements a risk mitigation plan for the organization. Process Description. OCTAVE risk assessment Framework entails eight steps:
- Establish risk measurement criteria
- Develop information asset profile
- Identify information asset containers
- Identify areas of concern
- Identify scenarios
- Identify risks
- Analyze risks
- Select Mitigation approach
Comparing NIST 800-30 vs. ISO 27005 vs. OCTAVE Allegro


Conduct security risk assessment with Planet 9
With Planet 9 security risk assessment service, you can be sure your risk assessment will be conducted appropriately, timely, and in accordance with best practices and regulatory requirements. A risk assessment results in a comprehensive risk assessment report with all necessary information about potential threats and vulnerabilities that may lead to a security risk, along with the threats’ likelihood (probability) and impact. The report also includes controls that the organization has implemented to mitigate the risks. Finally, our experts provide recommendations and approaches for addressing identified risks and developing a remediation plan to mitigate them. Contact Planet 9 to learn more about the risk assessment.







